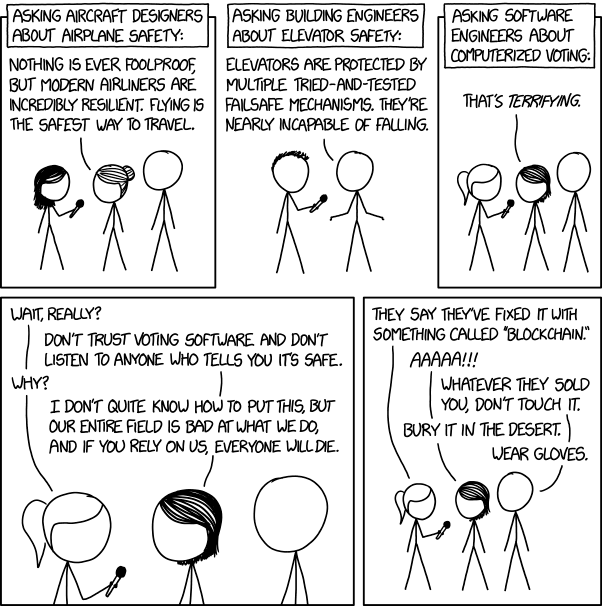
Let's talk about that xkcd voting machines comic


This image has stirred up a great deal of controversy and a bunch of people defending the state of software engineering.
I think y'all need a goddamn reality check, and I'm here to give it to you.
So this is mainly a response to something that crossed my Twitter feed in which Security Boulevard defends the current state of software engineering.
Most of us who agree with this kxcd comic lament the current state of software engineering - specifically the fact that there is very little actual engineering discipline involved in a lot of software today, including in the operating systems and other supporting software that underly mission-critical applications like voting machines. I am in a somewhat unique position in that I've got experience in all four domains used as examples in this comic:
- I am on the board of my cooperative apartment building, and as the only one with an engineering background most things mechanical come through me, and that includes elevator maintenance and repairs. Over the last 7 years I've received a moderate education in how elevators do what it is they do
- I am an FAA certificated private pilot, I own an airplane, and I actively participate in the maintenance of that airplane
- I have been writing, deploying, and maintaining software in production environments since the late 1990s. I have experience in environments ranging from startups to banks to ISPs to hospitals, and I've even done some government contract work
- I have been an election worker, and received training on both the electronic voting machines used in my district as well as the previous generation of mechanical "lever machines"
I'm telling you right now: Randal Munroe got it 100% right, and Security Boulevard is almost 180 degrees out of phase with reality.
Attack Versus Environment
A major thesis of the Security Boulevard piece, in fact the first criticism they level at the comic and what they call its biggest flaw, is "the comic confuses accidents vs. intentional attack."
Here's the thing: The two are not severable.
The counterexample for this is aircraft. Aircraft are under constant attack: Gravity wants them to fall from the sky and it is constantly banging at the gates trying to make that happen. It has lots of little helpers mounting other attacks to make that happen:
- Icing conditions foul the wings and spoil lift
- Storms produce turbulence violent enough to tear the wings from aircraft
- Microbursts steal lift from you during the most critical phases of flight (takeoff and landing)
- Low temperatures at altitude cause fuel to literally freeze on its way to the engine
These are all environmental attacks, and aircraft are built with defenses against them:
- Deicing boots and heated wing panels keep ice from fouling the wings
- Onboard weather radar helps pilots navigate around the most dangerous parts of storms
- Realtime weather monitoring at airfields warns of dangerous microbursts
- Aircraft fuel systems recirculate hot exhaust from the engines to preheat fuel
Aircraft are also hardened against active attacks by people, in part through policy and procedure (airside security at airports is pretty tight, even at the smaller fields I fly from people will stop you if you're poking at planes) and in part through design (Boeing and Airbus airliners are heavily computerized, but you can't access the avionics systems from the passenger WiFi - they're physically separate).
Voting machines do not benefit from this level of paranoid engineering discipline. They are fielded with bad security by design (standard hardcoded passwords, booting off USB sticks, Wireless networking enabled by default). The defense-in-depth approach used in aircraft (and by competent information security professionals) is, in many critical ways, absent. Instead these systems rely on compensating controls (election monitors sitting by the machine, storing them in secure warehouses, and if you're very lucky paper ballots that can be hand-verified later).
Hardware versus Software?
The Security Boulevard piece goes on to prevent a true statement: "The problems are as much hardware as software."
Here I certainly agree: A system is only as secure as its weakest link. Most general aviation aircraft locks are wafer-tumblers that are less secure than your average filing cabinet (in fact the key to open my plane's doors IS the key to my desk filing cabinet - it worked better than the key the plane came with, so I made copies of it). Once you're in the plane can be started by removing one screw and shorting two wires together - it's literally easier than all those scenes in movies where someone hotwires a car. The hardware is not robust against such attacks, and represents the weakest link.
They then go on to point out commonly observed problems when voting machines are audited, like USB ports which are accessible without a key (or with standard physical keys, photographs of which are widely available - because THAT'S never been a problem before).
Some attacks are impractical, like soldering on a JTAG, but they illustrate the need for strong process and procedure controls above and beyond what was used for mechanical voting systems.
The example here is actually another voting machine: New York's old lever machines were tamper-resistant because we performed an operational test and recorded the machine's counters at the start of the election - any malicious activity in the warehouse would be obvious (the voting lever interlocks would not function as intended, or counters would not advance correctly in testing when the curtain lever was returned). Such tampering is not evident in an electronic machine: Unless the case is opened you wouldn't know someone soldered on a JTAG. If the software is modified you won't know unless you perform an integrity check using secure and validated test tools. As of 2016 neither of these things was routine in my area, and security of the machines when not in use was less-than-adequate in my assessment.
What about compensating controls?
Security Boulevard rightly points out that the problem with electronic voting is a lack of accountability and fail-safes, and that experts want to see a verifiable paper trail (printed and approved by the voter or recorded on paper ballots) which is hand-counted to verify the election results. This is indeed what experts want, and what I want too.
It does NOT obviate the need for security on the voting machines.Wildly inaccurate election-day returns that bear no resemblance to the results of a hand-count undermine voter confidence. If we are not going to producce a system that is robust and accurate so as to be within epsilon of a theoretically perfect hand-count then we should not be producing a computerized electronic system AT ALL.
Additionally election-day returns in the east drive voter turnout further west in ways similar to exit polling: If the electronic system is telling folks their candidate is winning it may materially influence the election by lowering turnout. If that system is then wrong it could change a whole presidency.
...and all the rest?
Finally the article conclues by throwing up its hands: "It’s actually really hard for the Russians to hack voting machines, as they have to be attacked them on a one-by-one basis. It’s hard for a mass hack that affects them all. It’s much easier to target the back-end systems that tabulate the votes, which are more often normal computers connected to the Internet."
This is absolutely true. It's why voting machines need to be looked at as part of a SYSTEM, and the SYSTEM includes the back-end machines that tabulate the votes. Civil engineers don't plan drainage by hooking a big cistern up to a tiny outflow pipe and expecting it to magically swallow flood waters - they look at the SYSTEM and ensure that the back-end is as robust as the front-end.
Conclusion
The comic's humor rests on truth, in fact I would go so far as to say it's not humor so much as education presented in comic form. It applies basic standards common to every engineering discipline, including true and proper software engineering, and approaches the problem from the perspective of having a SYSTEM that produces accurate and repeatable results. Electronic voting is simply not robust enough to be trusted with something so critical as deciding the composition of our government.
The comic's assertion that "our entire field is bad at what we do" is certainly hyperbolic, but in this case it is the assumption we should be making, the same way we make that assumption in healthcare: Assume the software is broken and the system is owned.
Software engineering and information security is not yet robust enough to be the primary means of tabulating votes. It's probably OK for providing precinct-by-precinct election-day returns but we need to be taking a long, hard, critical look at the hardware, software, and procedures that comprise a voting SYSTEM before fully trusting it for even that purpose.
Comments
Display comments as Linear | Threaded
Neal McBurnett on :